DNS
UDP/53 -> TCP/53
DNS translates domain name to IP addresses.
Table of Contents
- DNS Record Types
- DNS Tools
- DNS Enumeration Using DIG
- Subdomain Enumeration
- Attacking DNS
DNS Record Types
| DNS Record | Description |
|---|---|
A | Returns an IPv4 address of the requested domain as a result. |
AAAA | Returns an IPv6 address of the requested domain. |
MX | Returns the responsible mail servers as a result. |
NS | Returns the DNS servers (nameservers) of the domain. |
TXT | This record can contain various information. The all-rounder can be used, e.g., to validate the Google Search Console or validate SSL certificates. In addition, SPF and DMARC entries are set to validate mail traffic and protect it from spam. |
CNAME | This record serves as an alias for another domain name. If you want the domain www.hackthebox.eu to point to the same IP as hackthebox.eu, you would create an A record for hackthebox.eu and a CNAME record for www.hackthebox.eu. |
PTR | The PTR record works the other way around (reverse lookup). It converts IP addresses into valid domain names. |
SOA | Provides information about the corresponding DNS zone and email address of the administrative contact. |
DNS Tools
DNS reconnaissance involves utilizing specialized tools designed to query DNS servers and extract valuable information. Here are some of the most popular and versatile tools in the arsenal of web recon professionals:
| Tool | Key Features | Use Cases |
|---|---|---|
dig | Versatile DNS lookup tool that supports various query types (A, MX, NS, TXT, etc.) and detailed output. | Manual DNS queries, zone transfers (if allowed), troubleshooting DNS issues, and in-depth analysis of DNS records. |
nslookup | Simpler DNS lookup tool, primarily for A, AAAA, and MX records. | Basic DNS queries, quick checks of domain resolution and mail server records. |
host | Streamlined DNS lookup tool with concise output. | Quick checks of A, AAAA, and MX records. |
dnsenum | Automated DNS enumeration tool, dictionary attacks, brute-forcing, zone transfers (if allowed). | Discovering subdomains and gathering DNS information efficiently. |
fierce | DNS reconnaissance and subdomain enumeration tool with recursive search and wildcard detection. | User-friendly interface for DNS reconnaissance, identifying subdomains and potential targets. |
dnsrecon | Combines multiple DNS reconnaissance techniques and supports various output formats. | Comprehensive DNS enumeration, identifying subdomains, and gathering DNS records for further analysis. |
theHarvester | OSINT tool that gathers information from various sources, including DNS records (email addresses). | Collecting email addresses, employee information, and other data associated with a domain from multiple sources. |
Online DNS Lookup Services | User-friendly interfaces for performing DNS lookups. | Quick and easy DNS lookups, convenient when command-line tools are not available, checking for domain availability or basic information |
DIG Queries
The SOA record is located in a domain's zone file and specifies who is responsible for the operation of the domain and how DNS information for the domain is managed.
Given IP and domain name
SOA
> dig soa www.inlanefreight.com
NS
> dig ns inlanefreight.htb @10.129.14.128
Version (If entry exists)
> dig CH TXT version.bind 10.129.120.85
Any (all available)
> dig any inlanefreight.htb @10.129.14.128
Zone Transfer
> dig axfr inlanefreight.htb @10.129.14.128
All Common dig Commands
| Command | Description |
|---|---|
dig domain.com | Performs a default A record lookup for the domain. |
dig domain.com A | Retrieves the IPv4 address (A record) associated with the domain. |
dig domain.com AAAA | Retrieves the IPv6 address (AAAA record) associated with the domain. |
dig domain.com MX | Finds the mail servers (MX records) responsible for the domain. |
dig domain.com NS | Identifies the authoritative name servers for the domain. |
dig domain.com TXT | Retrieves any TXT records associated with the domain. |
dig domain.com CNAME | Retrieves the canonical name (CNAME) record for the domain. |
dig domain.com SOA | Retrieves the start of authority (SOA) record for the domain. |
dig @1.1.1.1 domain.com | Specifies a specific name server to query; in this case 1.1.1.1 |
dig +trace domain.com | Shows the full path of DNS resolution. |
dig -x 192.168.1.1 | Performs a reverse lookup on the IP address 192.168.1.1 to find the associated host name. You may need to specify a name server. |
dig +short domain.com | Provides a short, concise answer to the query. |
dig +noall +answer domain.com | Displays only the answer section of the query output. |
dig domain.com ANY | Retrieves all available DNS records for the domain (Note: Many DNS servers ignore ANY queries to reduce load and prevent abuse, as per RFC 8482). |
Attacking DNS Sever/Dangerous Settings
| Option | Description |
|---|---|
allow-query | Defines which hosts are allowed to send requests to the DNS server. |
allow-recursion | Defines which hosts are allowed to send recursive requests to the DNS server. |
allow-transfer | Defines which hosts are allowed to receive zone transfers from the DNS server. |
zone-statistics | Collects statistical data of zones. |
DNSenum
dnsenum --enum inlanefreight.com -f /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -r
Subfinder
./subfinder -d inlanefreight.com -v
subbrute
git clone https://github.com/TheRook/subbrute.git
cd subbrute
echo "ns1.inlanefreight.com" > ./resolvers.txt
./subbrute inlanefreight.com -s ./names.txt -r ./resolvers.txt
Enumerating CNAME records
> host support.inlanefreight.com
support.inlanefreight.com is an alias for inlanefreight.s3.amazonaws.com
Zone transfer vulnerability
DNS server configured improperly -> unauthroized can perform zone transfer and get the entire DNS zone file; exposes a lot of info.
check if a website is vulnerable
dig axfr example.com @10.0.0.1
vulnerable:
example.com. 3600 IN A 192.168.1.1
internal.example.com. 3600 IN A 10.0.0.5
mail.example.com. 3600 IN MX 10 mailserver.example.com.
example.com. 3600 IN TXT "SPF=include:_spf.google.com"
secure:
; Transfer failed.
use fierce to enumerate all DNS servers from root whilst scanning for zone transfer vulnerability
fierce --domain zonetransfer.me
Subdomain Takeover
most companies use CDNs to host their content. They usually a subdomain pointing to that service
for example, here is a CNAME record
sub.target.com. 60 IN CNAME anotherdomain.com
sub.target.com points to anotherdomain.com, suppose anotherdomain.com expires, and we register and claim it, we basically took over sub.target.com
for example,
> host support.inlanefreight.com
support.inlanefreight.com is an alias for inlanefreight.s3.amazonaws.com
support.inlanefreight.com shows no such bucket, we can subdomain takeover by creating Amazon s3 bucket with the same name inlanefreight.s3.amazonaws.com
DNS Spoofing
redirect traffic to fraudulent website
Local DNS Poisoning
- modify such that legitimate domain points to attacker's IP
192.168.225.110
> cat /etc/ettercap/etter.dns
inlanefreight.com A 192.168.225.110
*.inlanefreight.com A 192.168.225.110
start Ettercap
Hosts > Scan for Hostsadd the target IP address (e.g.,
192.168.152.129) to Target1 and add a default gateway IP (e.g.,192.168.152.2) to Target2
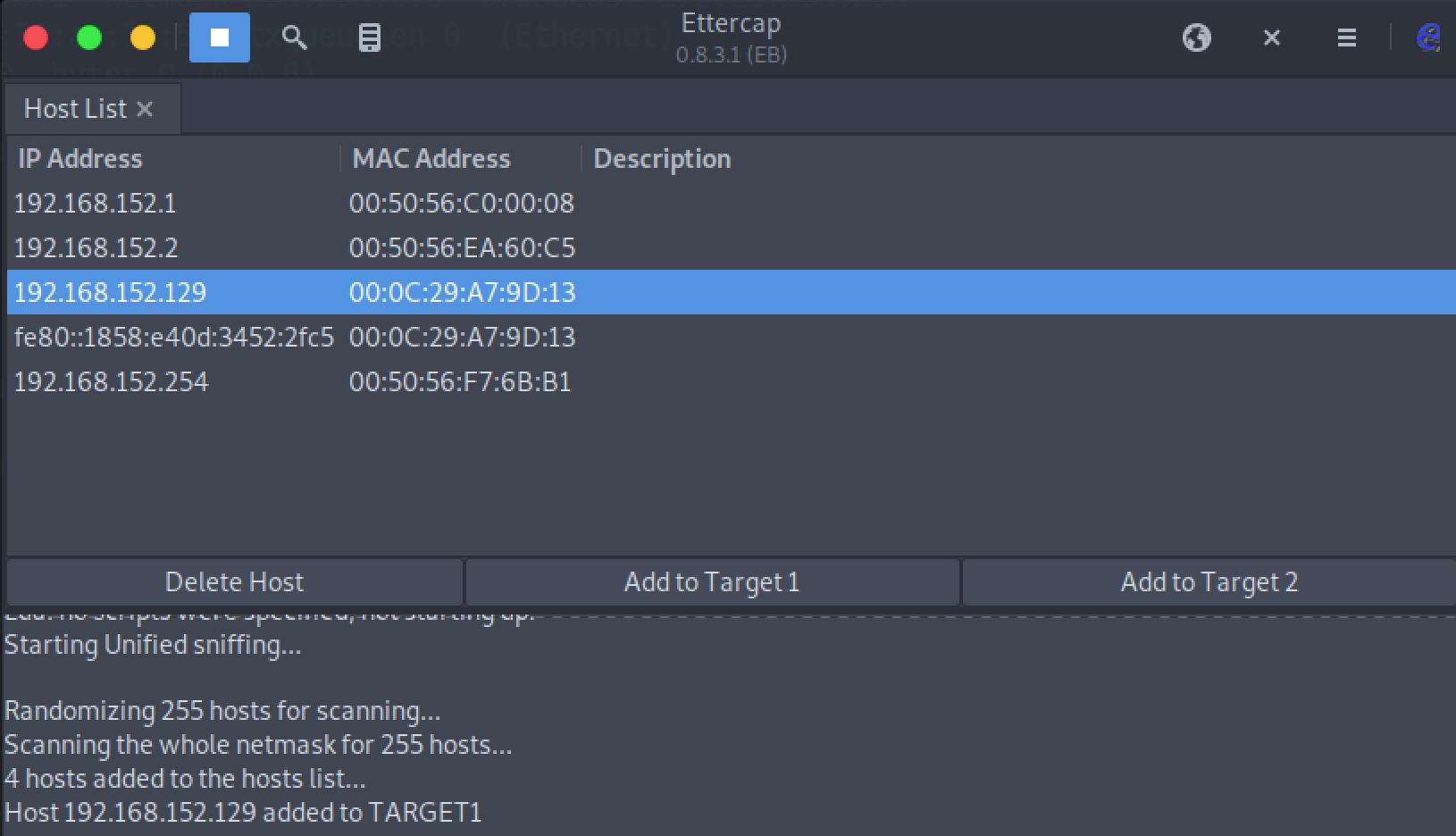
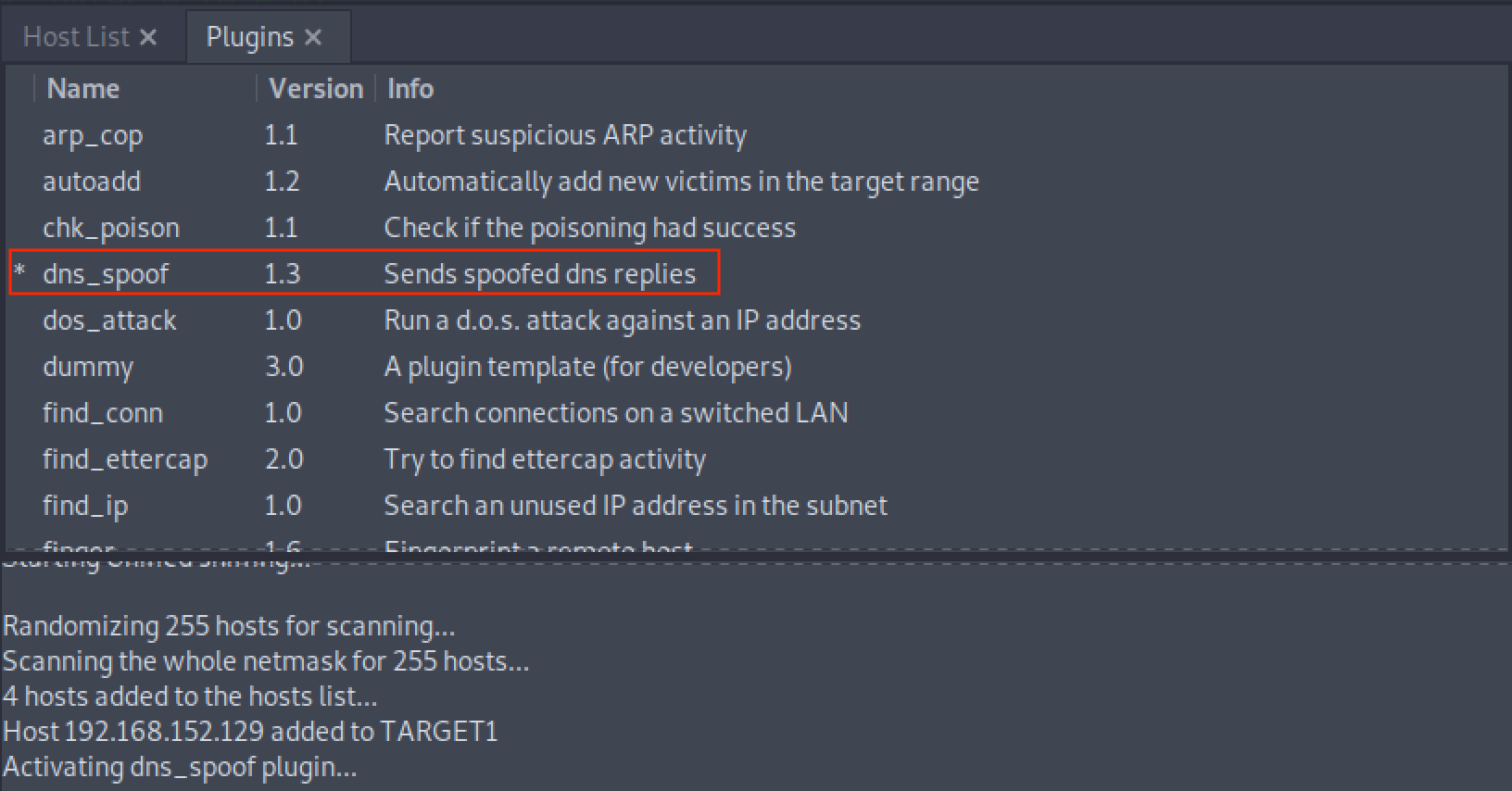
Activate
dns_spoofattack by navigating toPlugins > Manage Plugins. This sends the target machine with fake DNS responses that will resolveinlanefreight.comto IP address192.168.225.110
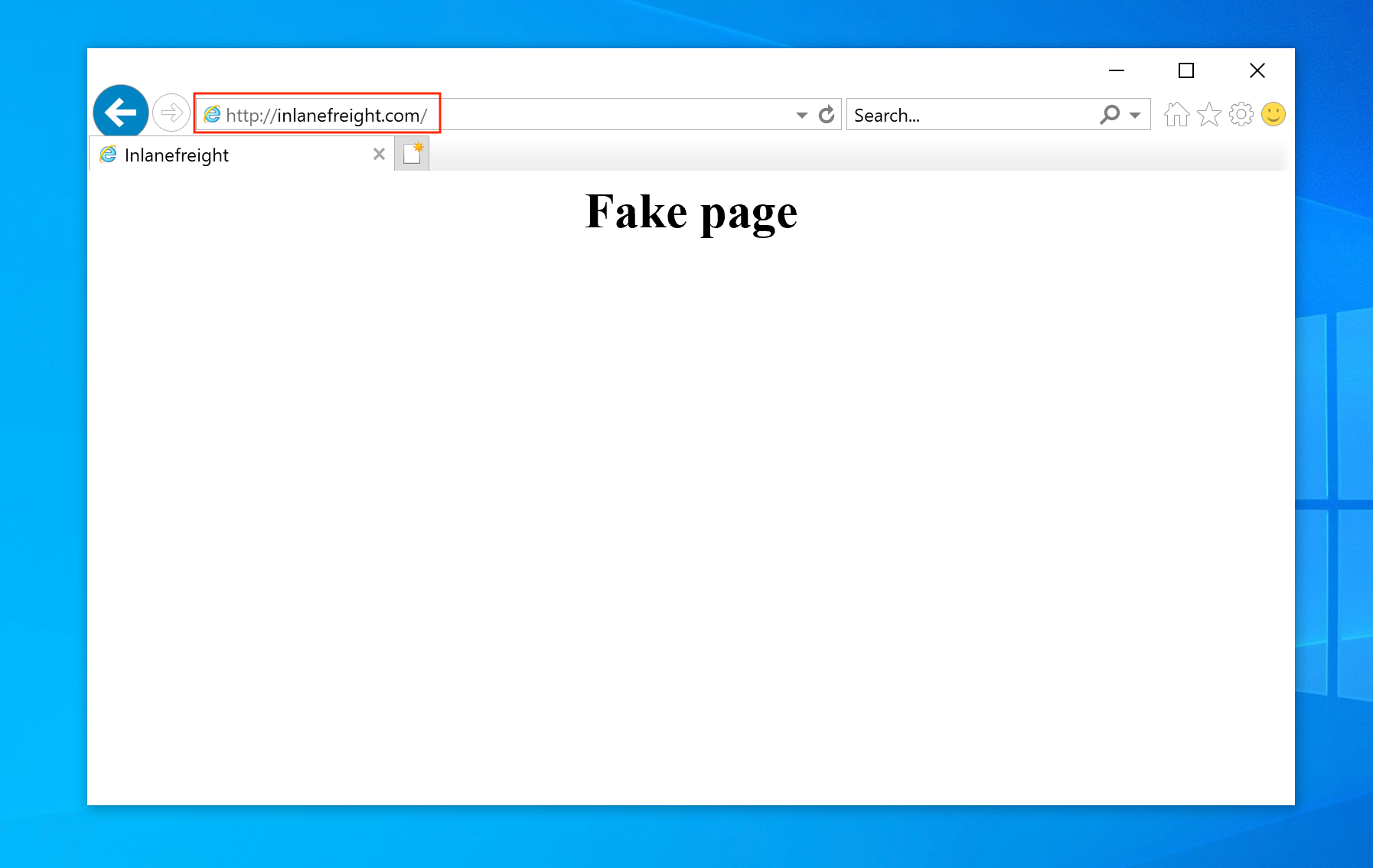
After a successful DNS spoof attack, if a victim user coming from the target machine
192.168.152.129visits theinlanefreight.comdomain on a web browser, they will be redirected to aFake pagethat is hosted on IP address192.168.225.110:
In addition, a ping coming from the target IP address 192.168.152.129 to inlanefreight.com should be resolved to 192.168.225.110 as well:
C:\>ping inlanefreight.com
Pinging inlanefreight.com [192.168.225.110] with 32 bytes of data:
Reply from 192.168.225.110: bytes=32 time<1ms TTL=64
Reply from 192.168.225.110: bytes=32 time<1ms TTL=64
Reply from 192.168.225.110: bytes=32 time<1ms TTL=64
Reply from 192.168.225.110: bytes=32 time<1ms TTL=64
Ping statistics for 192.168.225.110:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 0ms, Maximum = 0ms, Average = 0ms