Windows Credential Hunting
Table of Contents
- Windows Search
- Lazagne
very useful third party tool for clear-text creds - findstr
built in grep
A user may have documented their passwords somewhere on the system. There may even be default credentials that could be found in various files.
"Know how the target system is being used"
Take the example of an IT Admin Workstation:
What might an IT admin be doing on a day-to-day basis & which of those tasks may require credentials?
Keywords to consider:
| Passwords | Passphrases | Keys |
|---|---|---|
| Username | User account | Creds |
| Users | Passkeys | Passphrases |
| configuration | dbcredential | dbpassword |
| pwd | Login | Credentials |
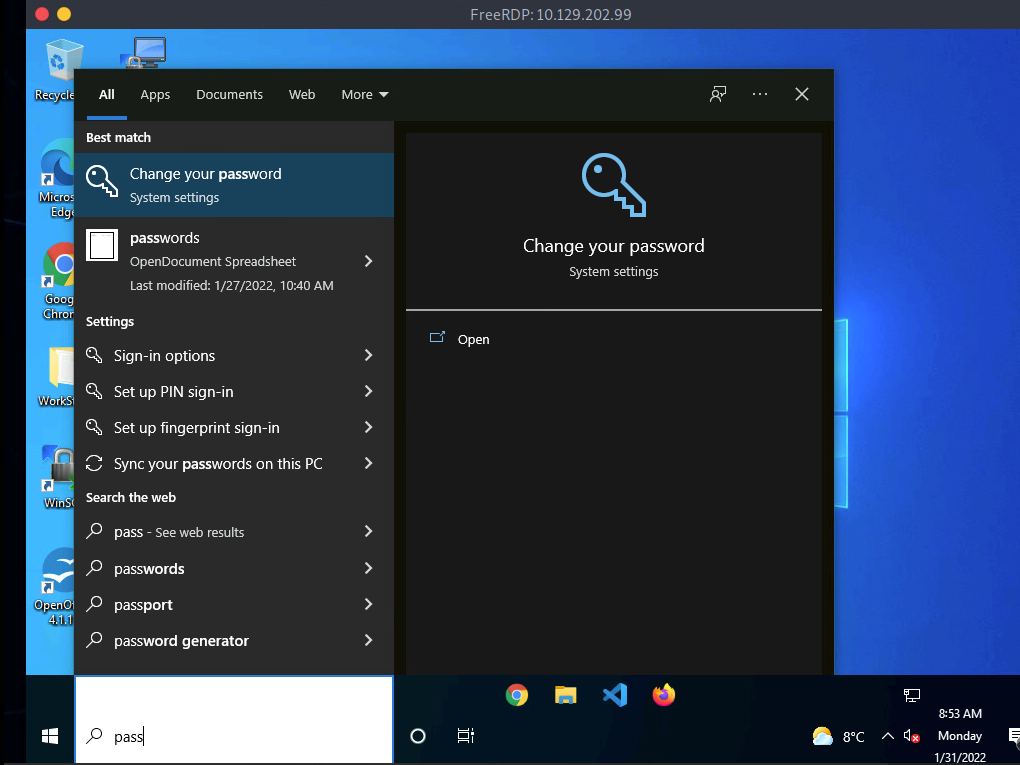
Windows Search
if we have access to a GUI
Lazagne
Lazagne quickly discover credentials insecurely stored by web browsers and other installed applications
transfer Lazagne.exe to target to run it (simply copy and paste if RDP)
C:\Users\bob\Desktop> start lazagne.exe all
findstr
C:\> findstr /SIM /C:"password" *.txt *.ini *.cfg *.config *.xml *.git *.ps1 *.yml