Network Traffic Analysis
Table of Contents
- BFS (Berkeley Packet Filter)
- NTA Workflow
- PDU (Protocol Data Units)
- MAC Addressing
- IPv4
- IPv6
- TCP Three-way Handshake
- TLS Handshake
- Wireshark
BFS (Berkeley Packet Filter)
BPF is a technology that enables a raw interface to read and write from the Data-Link layer. It provides filtering and decoding abilities.
NTA Workflow
- Ingest Traffic (capture traffic using tcpdump or Wireshark)
- Reduce Noise by Filtering
- Analyze and Explore
- Look at specific hosts, protocols, even things as specific as flags set in the TCP header
- Is the traffic encrypted or plain text? Should it be?
- Can we see users attempting to access resources to which they should not have access?
- Are different hosts talking to each other that typically do not?
- Fix and Monitor
PDU (Protocol Data Units)
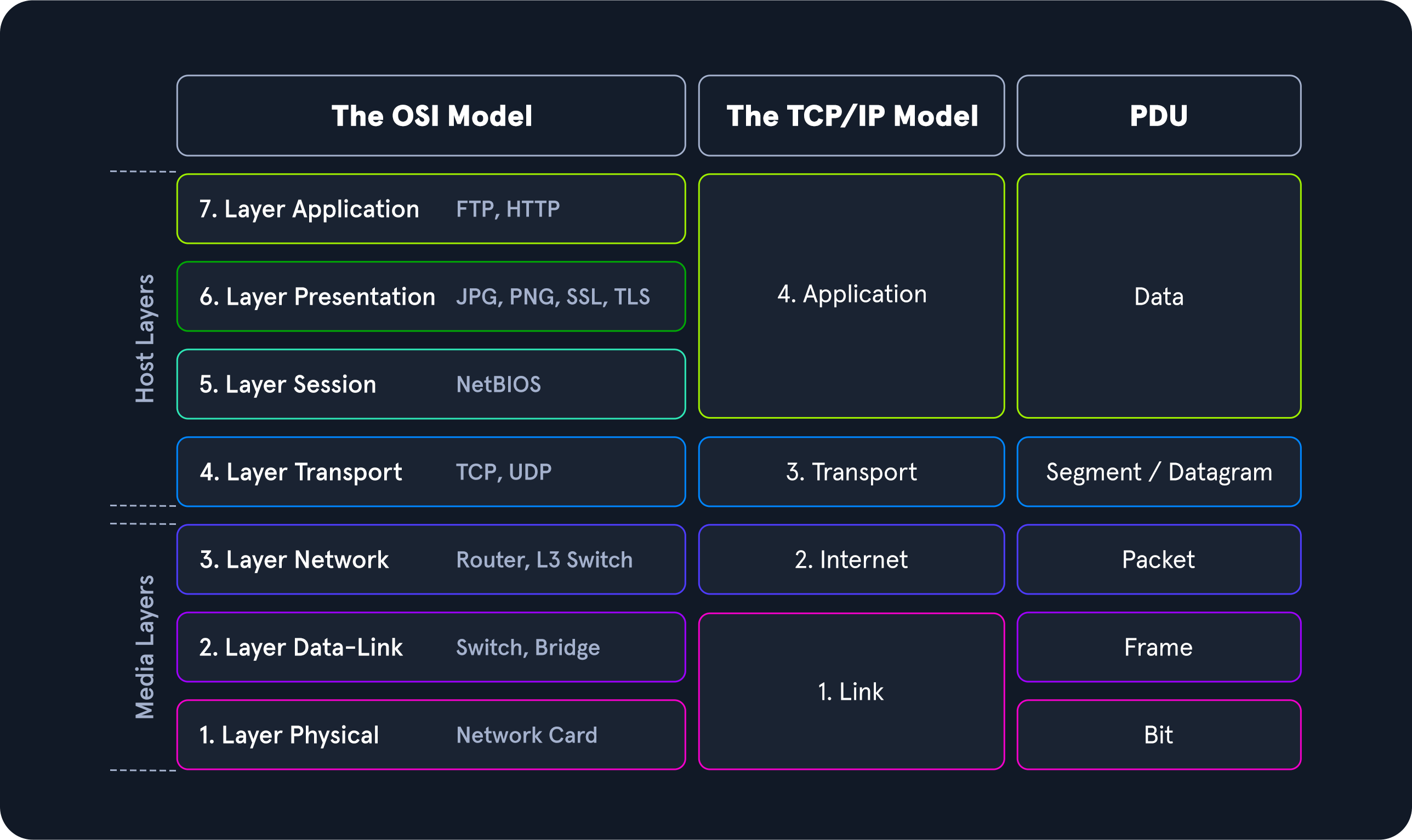
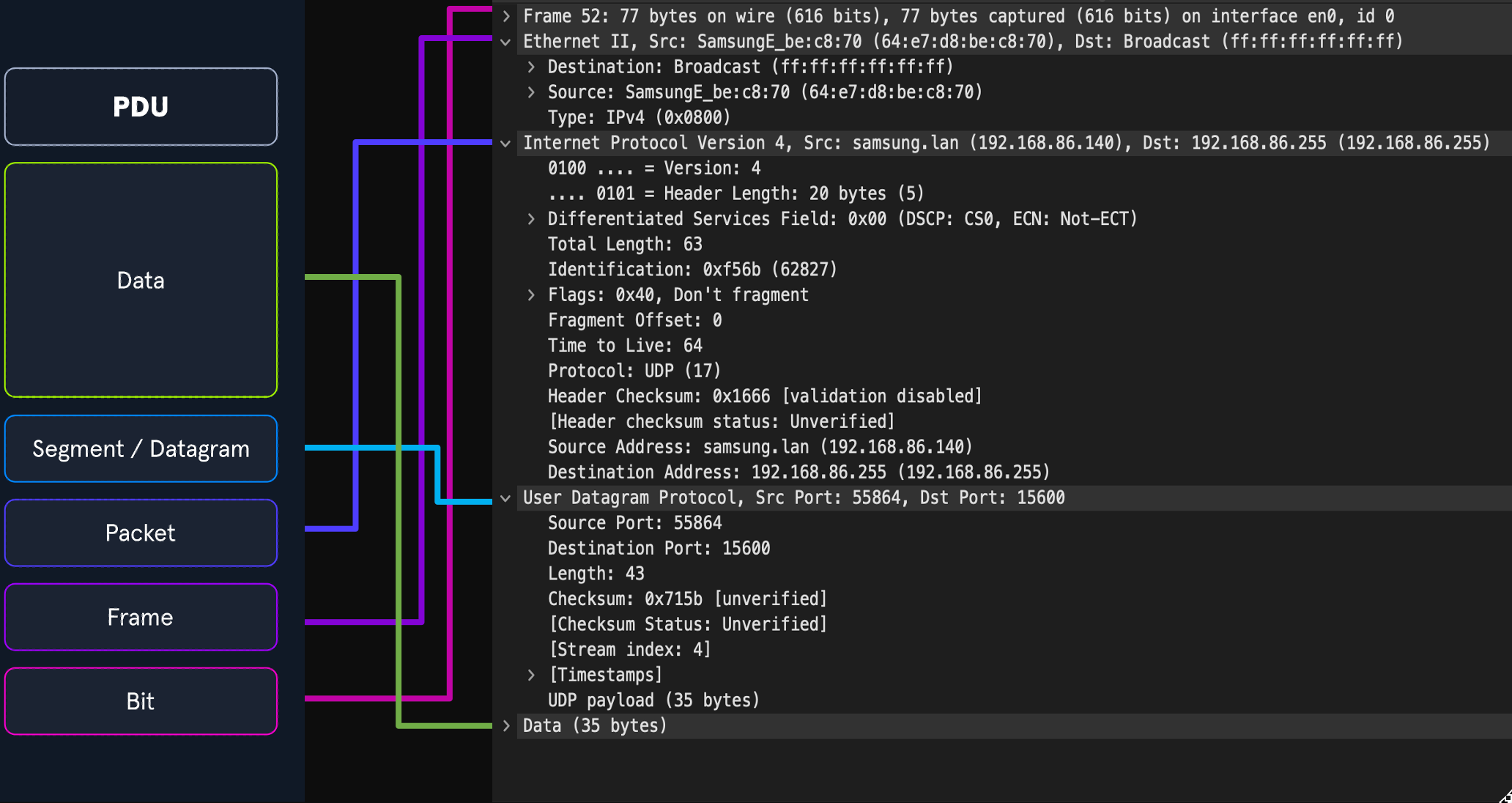
A PDU is a data packet made up of control information and data encapsulated from each layer of the OSI model
When inspecting a PDU, we need to keep the idea of encapsulation in mind. As our data moves down the protocol stack, each layer will wrap the previous layers' data in a new bubble we call encapsulation. This bubble adds the necessary information of that layer into the header of the PDU. This information can vary by level, but it includes what is held by the previous layer, operational flags, any options required to negotiate communications, the source and destination IP addresses, ports, transport, and application layer protocols.
MAC Addressing
media access control is the red arrow
Mac Addressing is utilized in layer 2 - Data LInk in OSI Model, and LInk layer in the TCP IP model
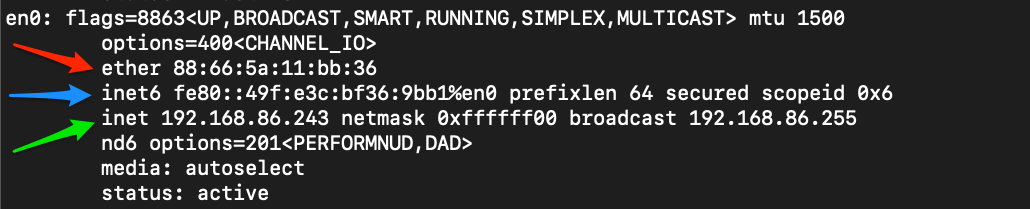
IPv4
Green arrow
When examining a PDU, we will find IP addresses in layer three (Network) of the OSI model and layer two (internet) of the TCP-IP model.
IPv6
Blue arrow
Along with a much larger address space, IPv6 provides:
- Better support for Multicasting (sending traffic from one to many)
- Global addressing per device Security within the protocol in the form of IPSec
- Simplified Packet headers allow for easier processing and move from connection to connection without being re-assigned an address.
IPv6 uses four main types of addresses within its schema:
IPv6 Addressing Types
| Type | Description |
|---|---|
Unicast | Addresses for a single interface (host to host) |
Anycast | Addresses for multiple interfaces, where only one of them receives the packet (one to many in a group where only one would answer) |
Multicast | Addresses for multiple interfaces, where all of them receive the same packet (one to many) |
Broadcast | Does not exist and is realized with multicast addresses |
TCP Three-way Handshake
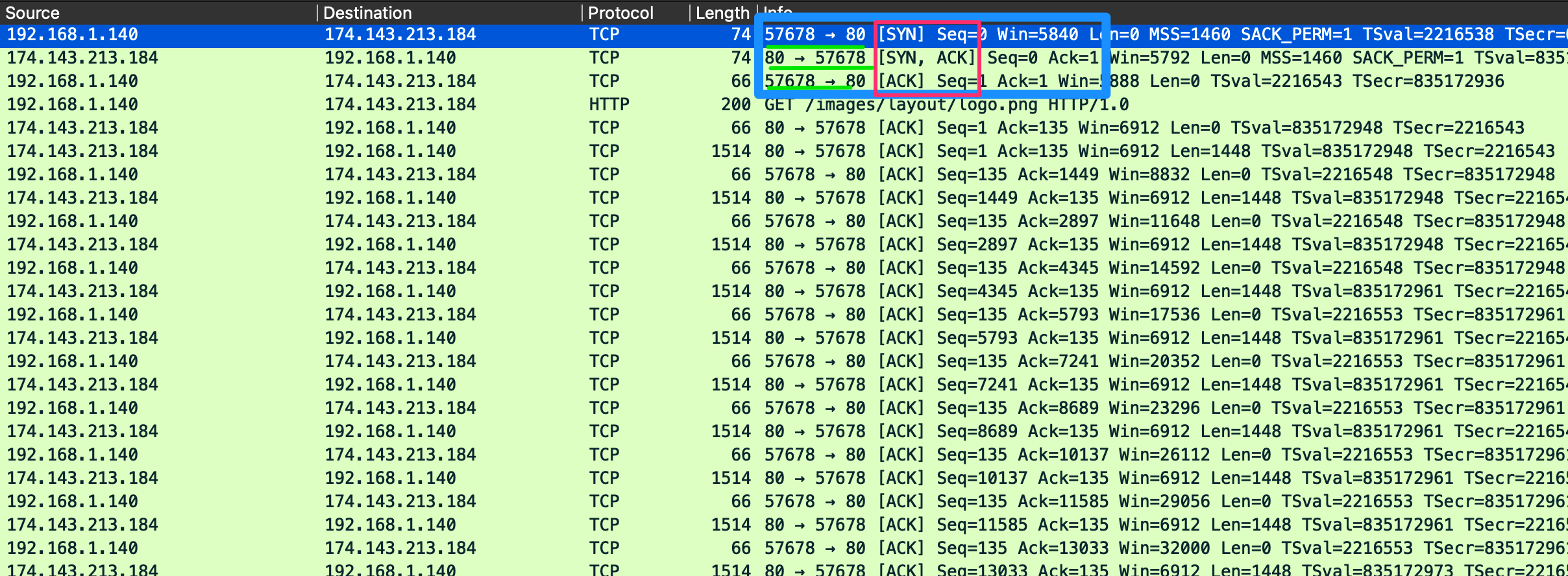
Client on random high port sends a SYN to port 80 in host. Host responds wit a Syn Ack, client responds with an ACK. After connection established, a png request is sent.
TCP teardown
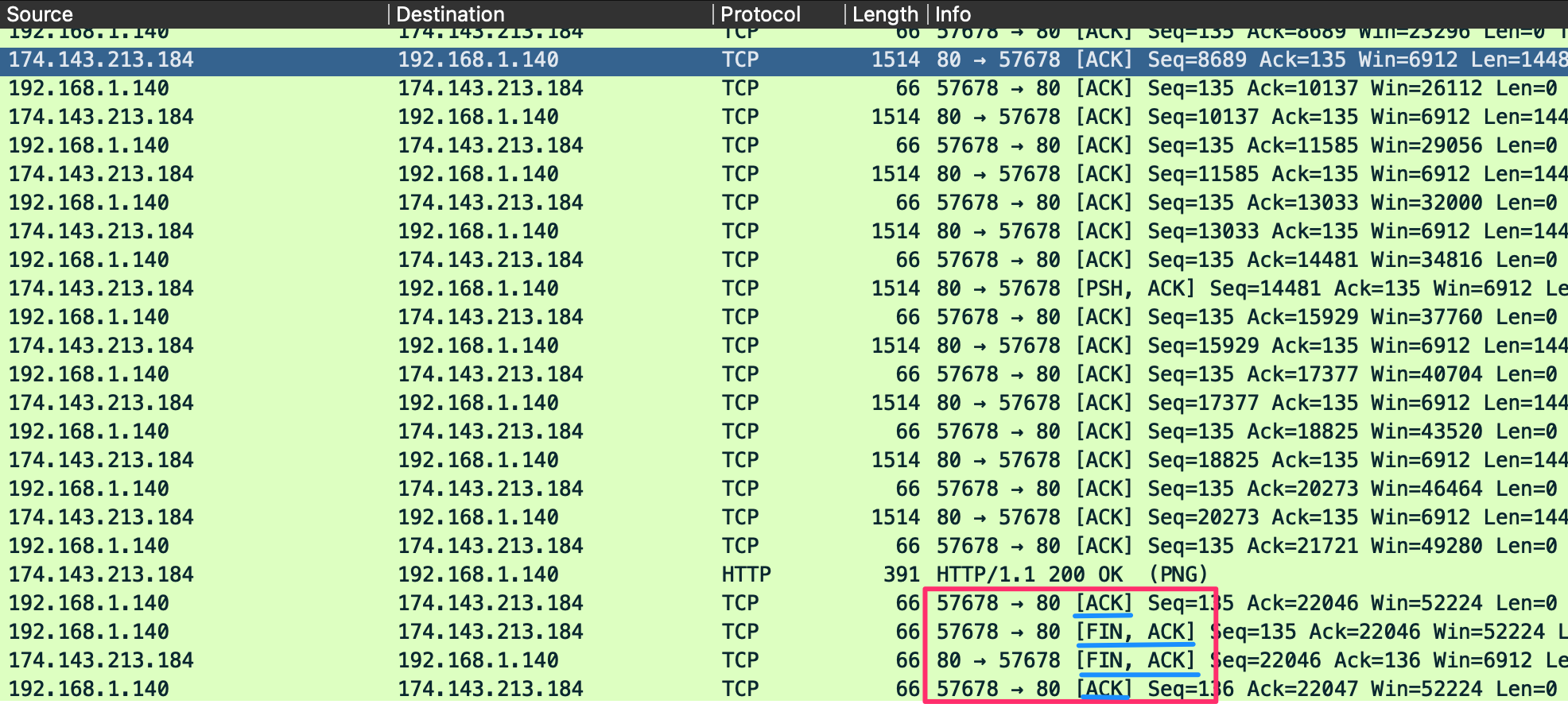
- FIN ACK
- FIN ACK
- ACK
TLS Handshake
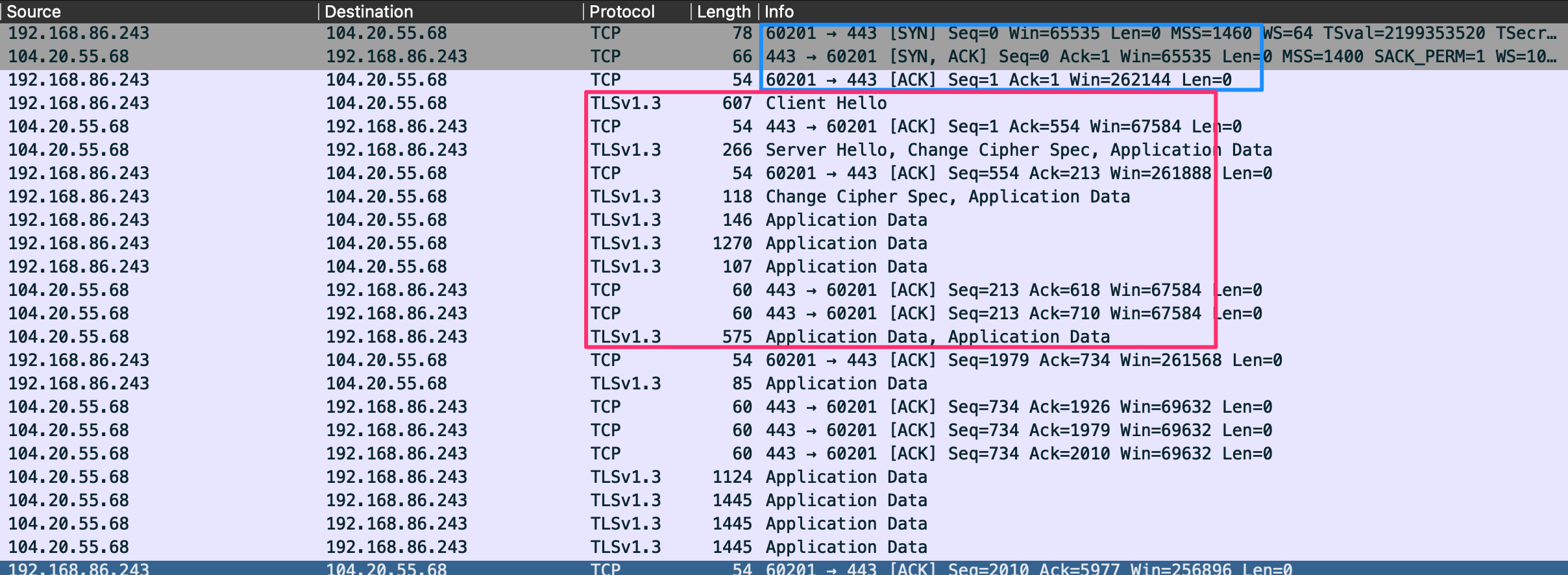
TLS handshake on HTTPS.
- Client and server exchange hello messages to agree on connection parameters.
- Client and server exchange necessary cryptographic parameters to establish a premaster secret.
- Client and server will exchange x.509 certificates and cryptographic information allowing for authentication within the session.
- Generate a master secret from the premaster secret and exchanged random values.
- Client and server issue negotiated security parameters to the record layer portion of the TLS protocol.
- Client and server verify that their peer has calculated the same security parameters and that the handshake occurred without tampering by an attacker.